Single Sign On (SSO) and Open Authorization (OAuth) are critical technologies commonly used to improve user experience and enhance online applications' security. In this blog post, we'll take a closer look at how SSO and OAuth work and how they can be used to improve user authentication.
Before going ahead, if you are interested in implementing these authorizations in your web app projects, it's always a good idea to reach out to a good web app development provider for quality development and implementation.
Let us begin with the single sign-on first.
What Exactly is Single Sign On?
SSO is a method of authenticating apps and websites with just one user's credentials. In short, one password for all other integrated app logins, like Google Workspace, Zoom, Asana, or Slack. Instead of an individual password, you only use one password to access all apps.
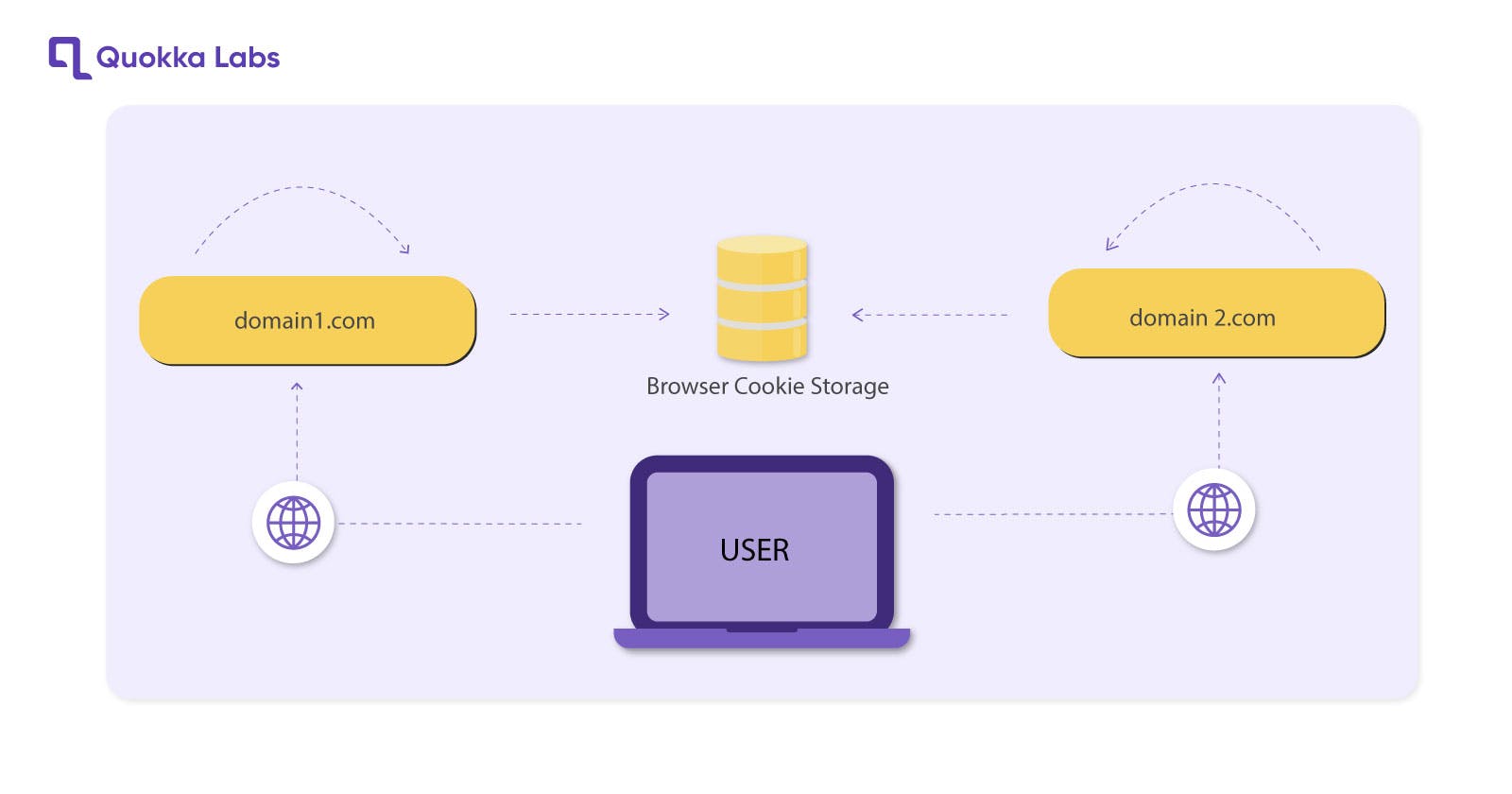
How Does Single Sign On (SSO) Work?
Users will be redirected to a central authentication server when accessing an SSO application. The user will then enter their login information, which the authentication server will verify.
If the login information is correct, the authentication server will generate a token that can be used to access the application. In the user's browser, the token is stored. It automatically logs users into any other applications they are authorized to access.
One of the main benefits of SSO is that it helps to improve security by reducing the number of times a user is required to enter their login information. It can help to lessen the danger of unauthorized access to sensitive data and protect against identity theft.
SSO also helps improve the user experience by eliminating the need to remember multiple login credentials, which can be a hassle for users who have to access various applications regularly.
Types of Single Sign-on (SSO)
Various types of SSOs exist, and they continue to develop new ones. Let's see some of the famous SSO types.
SAML – Security Access Markup Language
SAML (Security Assertion Markup Language) is an open standard protocol that securely exchanges authentication and authorization data between parties. It is commonly used in Single Sign-On (SSO) solutions to allow users to access multiple applications with a single login credential.
SAML allows a user to authenticate with a central identity provider, which generates a token that can be used to access other applications. It helps streamline the login process and improve the user experience by eliminating the need to remember multiple login credentials. SAML is widely used in the public and private sectors, and many applications and identity management systems support it.
Open Authorization (OAuth)
We will talk about this type briefly below the content.
OpenID Connect (OIDC)
OpenID Connect (OIDC) is an open standard protocol that approves users and authorizes them to contact resources. It is based on the OAuth 2.0 protocol and is easy to use and integrate with many applications. OIDC allows users to log in to applications using their existing credentials from a third-party identity provider, such as Google or Facebook.
OIDC also helps to improve security by allowing users to use strong, unique passwords and two-factor authentication (2FA) to protect their accounts. OIDC is widely used in the public and private sectors and is supported by various applications and identity management systems.
Kerberos
Kerberos is a network authentication protocol that gives secure communication over unsecured networks. It uses encryption and a trusted third party (called a Key Distribution Center, or KDC) to verify the identity of users and grant them access to network resources. Kerberos allows users to authenticate with the KDC, which generates a ticket that can be used to access network resources.
Kerberos is widely used in enterprise environments and is supported by many operating systems and applications.
Smart Card Authentication
It's a hardware-based facility that acts the same as SSO, as a physical smart card plugged into a computer. The software operates on the crypto keys on the smart card and authenticates the user. Smart cards are highly secure and need a PIN to use them.
What is OAuth?
Open Authorization (OAuth) is a standard protocol to grant third-party applications access to user data without requiring users to share their login credentials. OAuth works by generating a token that is used to authenticate the user's access to the data. It allows users to grant access to their data without revealing their login credentials, which can help to increase security and protect against unauthorized access.
OAuth is commonly used in Single Sign-On (SSO) solutions, and many applications and identity management systems support it. OAuth is also used to enable social media login functionality, allowing users to log in to applications using their social media accounts.
How does OAuth work?
Open Authentication OAuth allows users to grant access to their resources on one site (such as Google or Facebook) to another (such as a new application they want to use). It is accomplished through access tokens, unique codes that grant temporary, limited access to the user's resources. When users wish to give access to their resources, they are redirected to the site they want to grant access to, where they can log in and authorize the access.
Once the access is granted, the third-party site receives an access token, which it can use to access the user's resources. This process helps to ensure that user passwords are not shared with third parties, and that access to the user's resources is controlled and monitored.
If you are starting with mobile apps, it's better to know the fundamentals of developing them and keeping them away from security glitches:
Read More- A Step-by-Step Guide to Mobile App Development Process
OAuth 1.0 vs. OAuth 2.0
Open Authentication OAuth 1.0 and OAuth 2.0 are two versions of the OAuth open standard for authorization. OAuth 1.0 was released in 2007 and has since been superseded by OAuth 2.0, which was released in 2012. There are numerous vital variances between the two versions.
One significant difference is that OAuth 1.0 requires a cryptographic signature to secure the authorization process. At the same time, OAuth 2.0 relies on secure transport mechanisms such as SSL/TLS to ensure the authorization process. OAuth 1.0 also requires using complex cryptographic algorithms to generate the signature, which can be challenging to implement for some developers.
Another difference is that OAuth 1.0 only supports the authorization of resources, while OAuth 2.0 supports both authorization and authentication. It means that OAuth 2.0 can be used to verify the identity of a user as well as grant access to their resources. OAuth 2.0 also supports multiple authorization flows, which allows it to be used in a broader range of scenarios than OAuth 1.0.
Overall, OAuth 2.0 is a more flexible and secure version of the OAuth standard and is recommended for use in new projects. However, OAuth 1.0 is still in use in some older systems, and developers should know the differences between the two versions when working with OAuth.
Final Words
Single Sign On (SSO) and OAuth are powerful technologies that manage access to resources and applications. SSO and OAuth help improve security and convenience by simplifying the process of accessing resources and applications.
Suppose you want to implement SSO or Open Authentication OAuth in your application, but you need stress-free work; in that case, an experienced app development company can help.
Thanks for reading!